Navigating the Clouds – an Overview of Public Cloud and Private Cloud
Everything about the Cloud; Public and Private
Cloud computing has become a much needed asset today for organizations worldwide, with remote working, and working from anywhere (WFA) being a part of the new normal. With the types of cloud computing options available, selecting an efficient type that meets the exact requirements of a particular organization takes considerable time and effort.
This article aims to shed some light on the said evaluation process by giving an overview of public cloud and private cloud, their differences, common concerns of cloud computing and the security challenges faced alongwith. It aims to help you understand public and private clouds considerably and outline how best a cloud platform should be selected for an organization.
What is Cloud Security?
The collaboration of a set of controls, policies, technologies, and procedures to protect cloud-based systems, infrastructure, and data is identified as Cloud Security, also known as Cloud Computing Security. The configuration of these security measures is to support supervisory compliance and protect cloud data and customer privacy; these configurations enable setting authentication rules for individual or multiple users and devices. Cloud security can be configured to the exact business requirement by authenticating access to filter traffic fittingly for the enterprise needs. Since these rules can be managed and configured in one place, IT teams are empowered to focus on other business areas while administration overheads are reduced.
Delivery of cloud security functionalities depends on the cloud security solutions in place or on the individual cloud provider. However, the business owner and the solution provider will have a shared responsibility when it comes to the implementation of the cloud security processes. The Shared Responsibility Model is built up of three basic categories:
- Customer is fully responsible
- Both customer and cloud service are responsible
- Cloud service is fully responsible
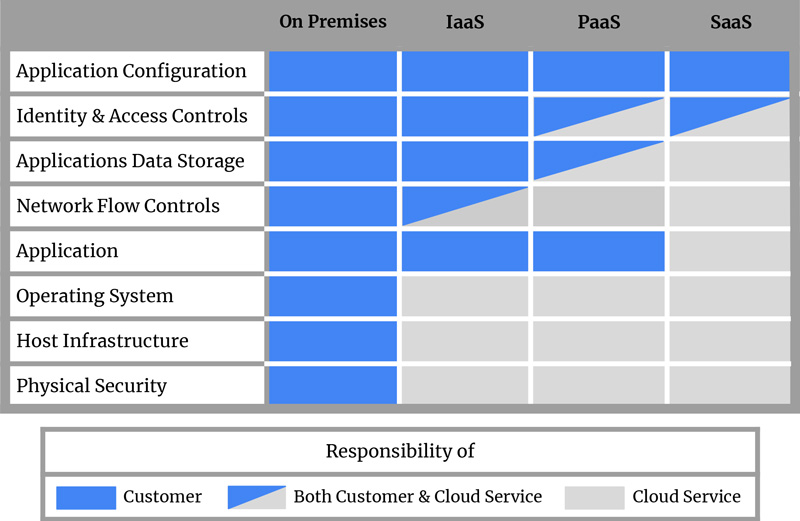
Types of Cloud Computing
Cloud Computing can be divided into four main categories: Public Cloud, Private Cloud, Hybrid Cloud, and Community Cloud.
Public Cloud: a service that is shared with multiple organizations using the public internet that is managed by a third-party service provider.
Private Cloud: an on-demand infrastructure and computing service that is dedicated to a single-user organization.
Hybrid Cloud: an infrastructure and computing service that is used as a mix of public and private clouds. The orchestration between the private cloud and the third party will be done by a Public Cloud Service.
Community Cloud: a hybrid form of a private cloud that enables different organizations to work on a shared platform with multi-tenant platforms.
Cloud services and cloud types are unique; choosing them would require a good understanding of your needs. Even if they are the same type, no two clouds are the same, and no two cloud services would be the exact same. But the understanding you can get about each Cloud Computing type and service would be helpful to your business according to how you plan on using them.
Public Cloud & Private Cloud
Providing IT infrastructure and services to the customers are the main responsibilities of Cloud Computing. There are five criteria that need to be fulfilled by a service for it to be known as a Cloud Service. They are as follows:
- On-demand self-service: the customers can decide on starting and stopping services without directly interacting with the provider.
- Broad Network Access: the service should be available for any device that is using any network.
- Resource Pooling: a pool of resources is created and dynamically allocated by the provider to the customers.
- Rapid Elasticity: the provided services by the provider should be quick and easily expandable.
- Measure Services: the usage of service should be measured and charged accordingly by the provider.
1. Public Cloud:
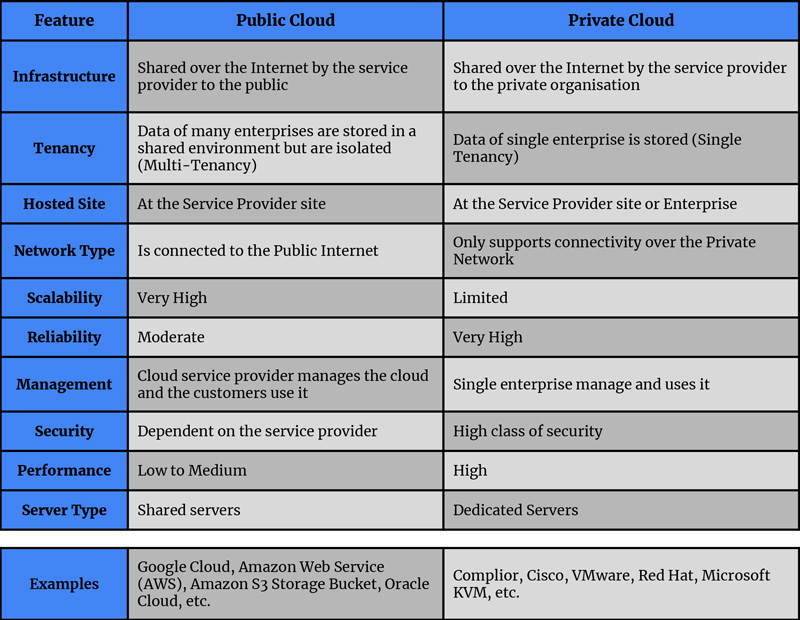
The Public cloud is a service that is shared with multiple organizations using the public internet that is managed by a third-party service provider. Server resources such as storage, applications, virtual machines, etc., are shared by the cloud service provider over the internet to the general public. For example, the cloud is being used by Google to run some of its applications such as YouTube, Google Docs, Google Sheets, Google Drive, etc. The ownership, deliveries, and operations are done by external cloud Service providers over the public internet.
If your company needs an infrastructure to host a large number of customers and work on projects that have different organizations, a Public Cloud would be a suitable option.
2. Private Cloud:
The Private Cloud is an on-demand infrastructure and computing service that is dedicated to a single-user organization. The service provider makes all resources public over the internet, but the connectivity is only supported over a private network. This network only has authentic users and single-occupant architecture. For example, Google runs some of its applications on the Public Cloud (applications such as YouTube, Google Docs, Google Sheets, Google Drive, etc.), but the back-end data of those applications are not available to the public since that type of data and applications are run on a Private Cloud. Only over a private network are the infrastructure and services deployed and maintained, and the software and hardware are dedicated only to a private company.
If your company needs an infrastructure that has high security, high performance, and privacy because of its flexibility and best adaptability, a Private Cloud would be a desirable option.
Difference between Public Cloud & Private Cloud
It’s crucial to do your homework before selecting a cloud solution to make sure that it will accommodate both your own workload and the demand of your company.
Top 03 Cloud Security Challenges in 2022
Due to technological advancements and how user-friendly the technology has become, nearly every person and organization has adopted cloud computing to varied degrees in both their personal and professional lives. It has been predicted that a record-breaking 60% of organizations will be using an external cloud provider’s managed service offering by 2022, doubling from 30% in 2018 -a trend that is likely to continue this year. However, with this adoption of the cloud comes the need to ensure that the organization has the capability of protecting against the top threats in Cloud Security.
Data Loss/Leakage
One of the many advantages of the cloud is that it makes sharing data stored in the cloud environment easier. This data on a Public Cloud environment could be accessed directly over the public internet, and it includes the ability to share the data within the environment with other parties by use of direct email invitations or by sharing a public link to the data.
(Note: To access data on a Private Cloud, the user should have access to the necessary private network.)
Sharing data with the use of public links or setting up a cloud-based repository for the public makes it accessible to whoever has the link; on the other hand, this makes it vulnerable to anyone with knowledge of the link. With the advancement of technology and the internet, there are tools to be found that exist specifically for searching the world wide web for unsecured cloud deployments.
Cloud Misconfiguration
An unencrypted data store that is left exposed to the general public is known as a Cloud Misconfiguration. All the global users of the same cloud platform could expose cloud data, leaving encryption keys and user credentials in open repositories. Cloud Misconfiguration could occur with any gaps, glitches, or errors that could expose the cloud environment to risk during cloud adoption.
Cloud Security misconfiguration is one of the most common cloud challenges in the present world since it allows anyone to access the store without any type of authentication over the internet. For example;
- A data set that belonged to Experian Credit Bureau that contained about 123 million American households’ private data was exposed due to a Cloud Misconfigured on Amazon S3 Storage Bucket in 2017.
- 3.5 million records, including Personally-Identifying Information (PII), were accidentally exposed by an LA-based non-profit organization, Los Angeles County 211, due to a Cloud Misconfigured on Amazon S3 Storage Bucket in 2018.
Inside Threats
An organization could be threatened by outsiders and insiders. Out of those two types of threats, inside threats are considered more dangerous since they are already inside the organization’s system. The cost to address an insider security problem has increased 34% since 2020, from $11.45 (117.19 SEK) million in 2020 to $15.38 (157.42 SEK) million in 2022. Insider-led incident frequency has also increased by 44% in 2022.
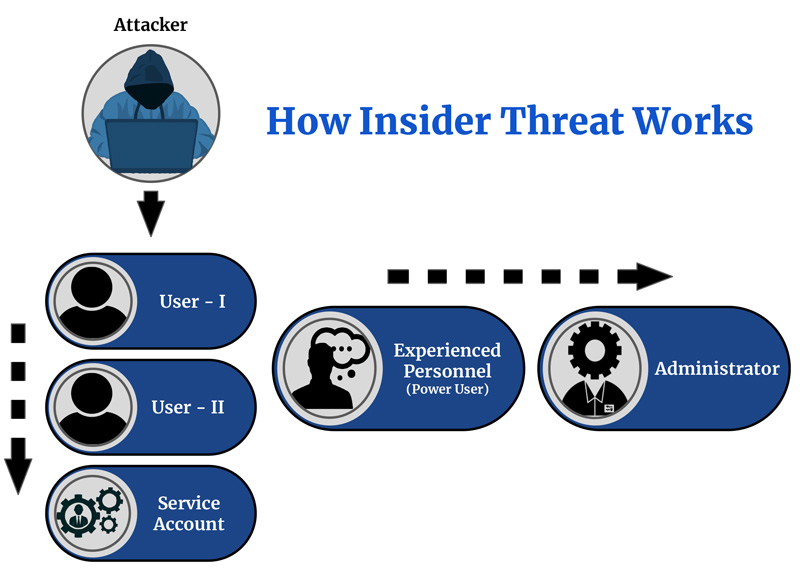
Insider threats could lead up to several other security challenges for an organization, such as misconfigured cloud servers, other employees within the organization falling prey to phishing emails, and employees storing sensitive and critical company data and figures on their own insecure personal devices.
Common Cloud Computing Questions
Which cloud type should I use?
The decision about a cloud type is up to the person and the business, depending on the specific requirements of each.
- Public Cloud: Predictable computing needs, apps, and services necessary to perform general IT and business operations, and environments with high volume workloads or fluctuating demands might be suited for a public cloud.
- Private Cloud: Private clouds may be well suited to handle highly classified sensitive data and for you to have more control over your data and the underlying infrastructure.
Which cloud is safest?
There is no correct answer to this question.
- Public Cloud: Due to multi-tenancy and numerous access points, public clouds tend to be subjected to a wider range of security threats. Public clouds often split the security responsibilities, and that single vulnerability in any split part could have an impact on the individual or organization. However, reputed public cloud providers have sophisticated mechanisms in place to identify and combat these threats.
- Private Cloud: Can be more secure than a public cloud, but that depends on how strong the cloud provider’s security is; Private clouds are more secure when they can only be accessed from their own network and only fewer people know about it.
But still, most would say that the answer to this question would be, “it depends!” and it is not wrong. Choosing a cloud type should be considered from the organization’s perspective, considering the advantages and disadvantages of each cloud type.
Which cloud costs more?
This is a loaded question; since if you talk about the raw cost and the cost it will save in the future with cloud challenges rapidly rising, the answers would be different.
- Public Cloud: Usually, the individual or the organization has to pay for what they have used in a public cloud, though public clouds such as Massachusetts Open Cloud does not charge for tenants.
- Private Cloud: Whoever sets up a private cloud is usually responsible for purchasing or renting new hardware and resources to scale up the security and services.
Conclusion
Every organization’s cloud strategy must cooperatively go with a security strategy with the continuous growth of cloud adoption. Businesses will continue to shift to cloud infrastructures assuming remote working and working from anywhere as part of the new normal. It is now more vital for organizations to have a reliable, strong, and robust cloud security strategy in place to host a safe and secure cloud infrastructure irrespective of the ongoing cyber threats. It is also helpful for organizations to prevent overspending or misspending on cloud security controls when they have a strategy in place.

