Table of Contents
Introduction: Why Growing Businesses Can’t Ignore Cyber Threats
Running a growing business is exciting — more customers, more data, more tools, more impact. But with growth comes a new wave of problems, and one of the biggest threats quietly waiting around the corner? Cyberattacks. And no, we’re not just talking about the classic viruses from the early 2000s.
These modern threats are smarter and more persistent. Hackers no longer just try to crash your systems — they study your operations, find weak spots, and sneak in undetected. They often sit quietly inside networks for weeks or even months before launching an attack, causing major damage before anyone notices.
That’s why basic antivirus software or a password update isn’t enough. Today’s business needs a smarter, more complete way to defend itself — something called advanced threat prevention. This approach combines smart tools, employee awareness, and a security-first mindset to help businesses fight back effectively without needing a full-time IT team or massive budget.
What Makes a Threat “Advanced”?
Not every cyber threat is a big deal — some are just annoying spam emails or random viruses. But advanced threats are different. These are carefully planned attacks that are hard to spot and harder to stop. They can involve multiple steps, different types of tools, and a high level of stealth.
Here’s what makes these threats so dangerous:
- They can change their tactics to avoid being caught.
- They use multiple entry points, including emails, websites, and even trusted software.
- They often go unnoticed while collecting valuable data.
- They are usually part of a larger, targeted plan, like stealing company secrets or demanding ransom.
For example, a cybercriminal might trick an employee into clicking a fake email link, use that to get access to your systems, and then move through your network silently. Weeks later, they might lock all your files and demand thousands of dollars to unlock them.
These are often part of Advanced Persistent Threats (APTs) or targeted ransomware attacks, sometimes hidden in software supply chains or even coming from inside your organization (insider threats). And then there are zero-day exploits — vulnerabilities no one knows about until it’s too late.
Advanced threats like these require a modern defense strategy — one that doesn’t just react, but actively monitors, blocks, and outsmarts attacks before they cause damage.
Key Strategies to Prevent Advanced Threats
Smarter Firewalls
Think of your business network like an office building. You wouldn’t leave the front door wide open. Firewalls work the same way — they block unwanted visitors from getting into your systems.
But traditional firewalls can only do so much. Next-generation firewalls are smarter — they not only block known threats but also watch for suspicious behavior. For example, if someone is trying to log in repeatedly with the wrong password, these systems can shut them out automatically.
Pairing this with alerts and basic system monitoring gives you a reliable first layer of defense.
Protecting Your Devices and Data Wherever They Are
Your endpoints — laptops, phones, and tablets — are often the easiest way for hackers to get in. That’s why it’s crucial to have software that watches those devices for odd behavior. Endpoint Detection and Response (EDR) is critical. If a computer suddenly starts sending strange files or connecting to unknown websites, the system can stop it or alert your team.
Even better, Extended Detection and Response (XDR) now connects information across different systems, so you can see how a threat might move from one device to another. This full-picture view helps prevent the spread of attacks and keeps your network safe.
Keep Software Updated — Always
One of the easiest ways to protect your business is also one of the most overlooked: keeping software updated. Hackers often look for old versions of programs that have known weaknesses. Updating your systems is like fixing cracks in a wall — it stops attackers from getting in. Regularly updating systems to fix security gaps is Patch management.
Set your computers and tools to update automatically, and regularly review which systems might still be out-of-date. It’s a simple step that can make a huge difference.
DNS Filtering & Deception Technology: Outsmart Attackers
Many cyberattacks start when someone clicks a malicious link. This is where DNS filtering steps in. It blocks access to known malicious domains before a connection is even made — like killing a scam call before it rings.
There’s also a clever strategy called deception technology, where fake systems or “honeypots” are set up to trick hackers into revealing themselves. These don’t interfere with your normal operations, but they quietly gather information to improve your defenses.
Notice Unusual Behavior Before It’s Too Late
Cyber threats don’t always come from strangers. Sometimes they come from someone inside your organization — or from hackers pretending to be a trusted employee. That’s why some systems now focus on behavior rather than just files.
They look for activity that doesn’t fit the usual pattern — like someone trying to download all your customer data late at night or accessing areas they never needed before. When something feels off, the system sends an alert so your team can investigate right away.
Work Together — Share What You Know
The truth is, you don’t have to fight cyber threats alone. Many businesses share information about the types of attacks they’ve seen so others can avoid them. There are networks and groups like Cyber Threat Intelligence (CTI) feeds, industry groups, and Information Sharing and Analysis Centers (ISACs) you can join to get early warnings and helpful insights.
Joining these communities helps you detect attacks before they hit your business — making threat mitigation a team effort.
Zero Trust & Micro‑Segmentation: Trust No One, Verify Everything
One of the most powerful mindset shifts in cybersecurity is called Zero Trust. It’s a simple idea: never assume anything is safe, even if it’s already inside your systems — “never trust, always verify.” This means checking every user and every device — all the time. It might sound strict, but it keeps hackers from moving freely if they manage to get in.
Add micro-segmentation, and you get extra layers of safety. When you separate different parts of your system (like customer data from employee records), it limits the damage a hacker can do.
Businesses using Zero Trust with segmentation have reported a dramatic drop in breach severity — especially in remote and cloud-first environments.
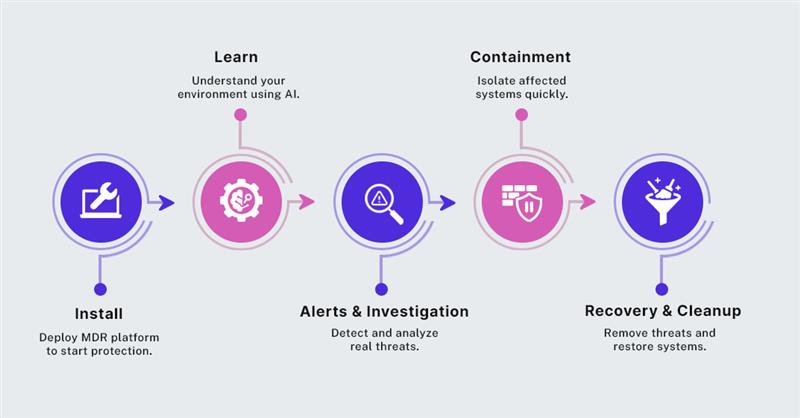
Managed Detection and Response (MDR): Expert Eyes on Your Cyber Perimeter
If you don’t have an in-house security operations center (SOC) — and most growing businesses don’t — Managed Detection and Response (MDR) gives you that capability without the heavy investment.
MDR is a service that combines advanced threat detection technology with human expertise. Think of it as outsourcing your cybersecurity command center to a team of specialists who monitor, detect, investigate, and respond to threats 24/7 — often before you even know there’s a problem.
eBuilder Security provides 24/7 protection with fast threat detection and response — stopping attacks in as little as 3 minutes. Our experts combine AI and human insight to keep your business secure around the clock.
We go beyond alerts with proactive threat hunting and full compliance support, so you can focus on growing your business while we handle the cybersecurity.
How to Start — Without Overwhelm
Start With What’s Most At Risk
Security planning starts with clarity. Ask yourself: What data matters most? Where are we most vulnerable? And how ready are we if something goes wrong? These questions help you identify your top priorities. You don’t need to overhaul everything at once. Start small — update your systems, train your team, and implement basic monitoring. By addressing the highest risks first, you create a strong foundation for broader security improvements.
Make Security Part of Company Culture
Technology alone isn’t enough — your employees play a central role in keeping your business safe. Even the most advanced security systems can’t stop someone from clicking a malicious link. That’s why it’s essential to build a culture of awareness. Invest in ongoing training that’s simple and engaging. Run simulated phishing tests. Reward employees for practicing good security habits. Over time, these efforts turn your team into a frontline defense that instinctively puts security first.
Complorer, by eBuilder Security is a fully managed security awareness training solution that takes the burden off your team by handling everything from administration to phishing simulations.
With role-based nano-trainings, multi-format learning methods, and real-time progress tracking, the platform delivers personalized and engaging education on emerging threats. Its automated phishing testing, including advanced spear phishing simulations using OSINT, keeps employees sharp and compliant. Through progressive training modules tailored to your organization’s needs and branding, your team continuously evolves — all while you stay focused on your core business.

Test, Improve, and Stay Compliant
Security isn’t a one-time setup — it’s an ongoing process. Regular testing is critical. Conduct scheduled system checks, bring in ethical hackers to uncover weak spots, and refine your defenses accordingly. At the same time, ensure your practices align with relevant data protection laws. If you handle customer data — and most businesses do — compliance is not optional. The steps you take to improve security will also reduce legal risks and boost customer trust.
Conclusion: Protect What You’re Building
To understand if your cybersecurity efforts are working, track a few simple metrics. Start with how quickly you detect threats and how fast your team responds — these are key indicators of resilience. Keep an eye on the number of incidents prevented and monitor how well your employees perform in phishing simulations. These scores reflect how effectively your team is adapting and learning. And don’t forget the financial side: if your improved defenses helped prevent even one serious breach, the savings could be significant — both in money and reputation.
Your business is growing, and that success is worth protecting. Cybersecurity isn’t just about preventing attacks; it’s about ensuring your future. With the right mix of tools, training, and proactive strategies, you can create a security foundation that supports — not stifles — your growth. Don’t wait until a crisis hits. Start now with a clear-eyed assessment of your vulnerabilities. Invest in your people. Upgrade your systems. Because true progress happens when ambition and protection grow together.

